How to Enable SSH-Agent Forwarding Permanently on WSL Ubuntu

- What is the ssh-agent used for?
ssh-agent is a program that helps you manage and securely store your SSH (Secure Shell) keys, making it easier to use SSH for secure authentication to remote servers and services. SSH keys are cryptographic keys used to authenticate your identity when connecting to remote servers or services over a network.
Here's how ssh-agent works:
- Key Storage: When you generate an SSH key pair (a public key and a private key), you can add your private key to the
ssh-agent. The private key is a secret, and it's important to keep it secure.ssh-agentprovides a secure and centralized way to store and manage these private keys. - Passphrase Protection: When you add a private key to
ssh-agent, you can (and should) protect it with a passphrase. This passphrase acts as an additional layer of security. When you use the key for authentication, you'll need to enter the passphrase to unlock the private key stored inssh-agent. - Key Authentication: Once your private key is added to
ssh-agent, you can use it to authenticate to remote servers without having to manually enter your passphrase each time. When you attempt to connect to a remote server that requires SSH authentication,ssh-agentautomatically provides your private key, and if needed, prompts you for the passphrase. - Agent Forwarding:
ssh-agentcan also be configured to forward your authenticated SSH sessions to other servers. This is useful when you need to authenticate to one server and then access another server from there without re-entering credentials.
This is the command to start ssh-agent.
eval 'ssh-agent'or
eval "$(ssh-agent -s)"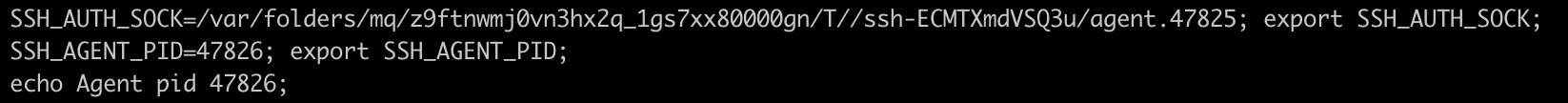
Note: this command will start ssh-agent , if it's not already running and provide output like: Agent pid 12345. If it's already running, it will provide information about the existing agent.
2. What is the ssh-agent forwarding used for?
Agent Forwarding: ssh-agent can also be configured to forward your authenticated SSH sessions to other servers. This is useful when you need to authenticate to one server and then access another server from there without re-entering credentials.
For example, local machine(IP1) -> hostA(IP2) ->hostB(IP3)
Scenario 01: Local machine wish to connect host A without private key.
ssh-add -K
or
ssh-add ~/.ssh/your_private_key
or
ssh-add /path/to/your-key-fileIf your key is protected with a passphrase, you'll be prompted to enter it.
*You can verify that your key has been added to ssh-agent by running:
ssh-add -l
*Use ssh-agent for SSH Authentication: Now, whenever you connect to a remote server using SSH, ssh-agent will automatically provide your SSH key for authentication, and you won't need to enter your passphrase each time. For example, to connect to a server, you can use a command like
ssh username@remote-server*Stopping ssh-agent: If you need to stop ssh-agent for any reason, you can use the following command:
ssh-agent -kThis will kill the ssh-agent process.
Scenario 02: On hostA, wish to connect host B with the private key on local machine.
Solution 1:
Enter ~/.ssh/config and add commands as follows.
Host IP2
ForwardAgent yesSolution 2:
When connecting to a remote server using SSH, use the -A option to enable agent forwarding. For example:
ssh -A username@remote-serverScenario 03: How permanently enable this ssh-agent forwarding function on WSL Ubuntu. (It's worth noting that when you log out of your session, the ssh-agent process is typically terminated automatically, and you'll need to start it again when you log in or when you open a new terminal session. You can automate the startup of ssh-agent by adding the necessary commands to your shell profile script (e.g., ~/.bashrc, ~/.bash_profile, or ~/.zshrc) to ensure it runs whenever you log in.)
1. Add eval 'ssh-agent' to ~/.profile.
2. AddKeysToAgent option in your SSH configuration file to control whether SSH keys used for authentication should be automatically added to the SSH agent. For example:
~/.ssh/config
Host IP2
AddKeysToAgent yes # No.1 Added
IdentityFile ~/.ssh/your_private_key # No.2 Added
ForwardAgent yes The purpose of AddKeysToAgent is to streamline the process of managing SSH keys. When it's set to "yes," any SSH key used for authentication during an SSH session is automatically added to the SSH agent. This eliminates the need for you to manually add the keys to the agent using the ssh-add command.
The primary purpose of IdentityFile is to allow you to specify which private key should be used for authentication when you have multiple SSH key pairs stored on your system. This is particularly useful when you want to use a specific key for a particular remote server or when you need to use different keys for different hosts.
Command-Line Option instead of IdentityFile : You can also specify the private key file using the -i (identity file) option with the ssh command. For example:
ssh -i ~/.ssh/my_private_key username@remote-serverBy using IdentityFile, you can avoid the need to specify the -i option every time you connect to a server and ensure that the correct private key is automatically used for authentication.
Conclusion:
The best solution to enable ssh-agent forwarding permanently on WSL Ubuntu as follows:
1. Add eval 'ssh-agent' or eval "$(ssh-agent -s)"to ~/.profile.
2. Enter ~/.ssh/config file and add commands as follows.
Host IP2
AddKeysToAgent yes
IdentityFile ~/.ssh/your_private_key
ForwardAgent yesssh-agent forwardingconnection command.
ssh username@remote-server
